Shift Left Security
Fix vulnerabilities, secrets, and misconfigurations early in the SDLC
The Challenge
Development, DevOps, and Security Teams Are Operating in Silos
The benefits of Shift Left Security are clear. However, putting this process into practice is more difficult. Although there are security tools that scan either IaC templates or container images, many don’t do both or lack integration across the software development lifecycle.
Developers need to identify vulnerabilities and security issues while shipping code quickly.
DevOps teams must manage policies and create integrations for multiple tools, duplicating efforts and hindering consistency.
Security teams struggle with siloed solutions, lack of shared context, and contradictory alerts.
Our Approach
A Unified Platform to Bring Teams Together Across the Application Lifecycle
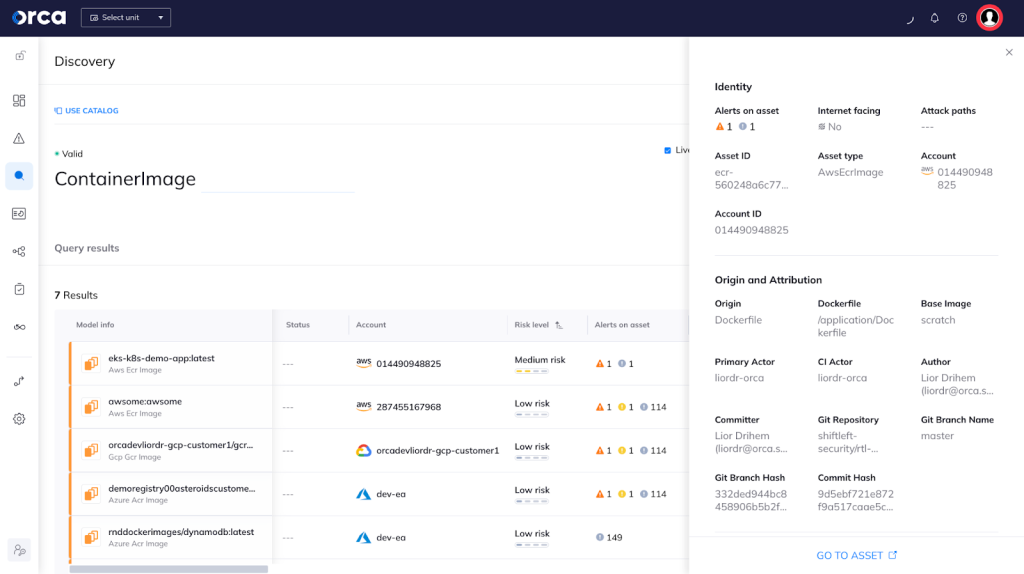
The Orca Cloud Security Platform provides comprehensive security and compliance checks across the full software development lifecycle, including IaC template and container image scanning. In addition, Orca traces findings from the production environment back to the original application development artifacts, ensuring security teams can partner with development and DevOps teams to fix risks quickly. Orca investigates the data and control plane for vulnerabilities, misconfigurations, malware, IAM risks, lateral movement risks and sensitive data exposure across the entire lifecycle of your applications.
Build
Container images and IaC templates are scanned on the developer desktop or as part of regular, continuous integration (CI) / continuous delivery (CD) workflows.
Deploy
Registries are continually monitored to ensure application images are secure before deployment, with guardrail policies in place to prevent insecure deployments.
Run (and Back Again)
Production environments are monitored for risks with contextual alerts and risk prioritization, as well as integrations with ticketing and notification tools.
Embed security from dev to cloud, and back to dev
Remediating cloud risks is a huge challenge for security teams, especially in a world where DevOps is the norm. With Orca Security, security teams can attribute risks immediately to the line of code that led to the risk reaching production.
- Insert security policy early to cut down the number of problems that make it to production
- Orca’s automation ensures risks are identified quickly with the ability to trace them back to the line of code that caused the issue
- Security teams save time tracking down development and DevOps teams to ensure remediation happens efficiently
- Improve your overall cloud security posture while reducing friction across your organization
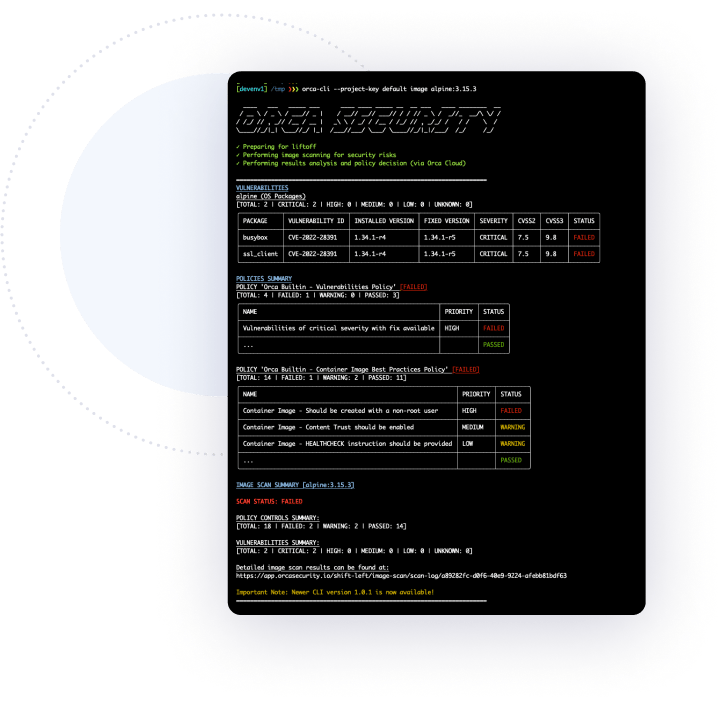
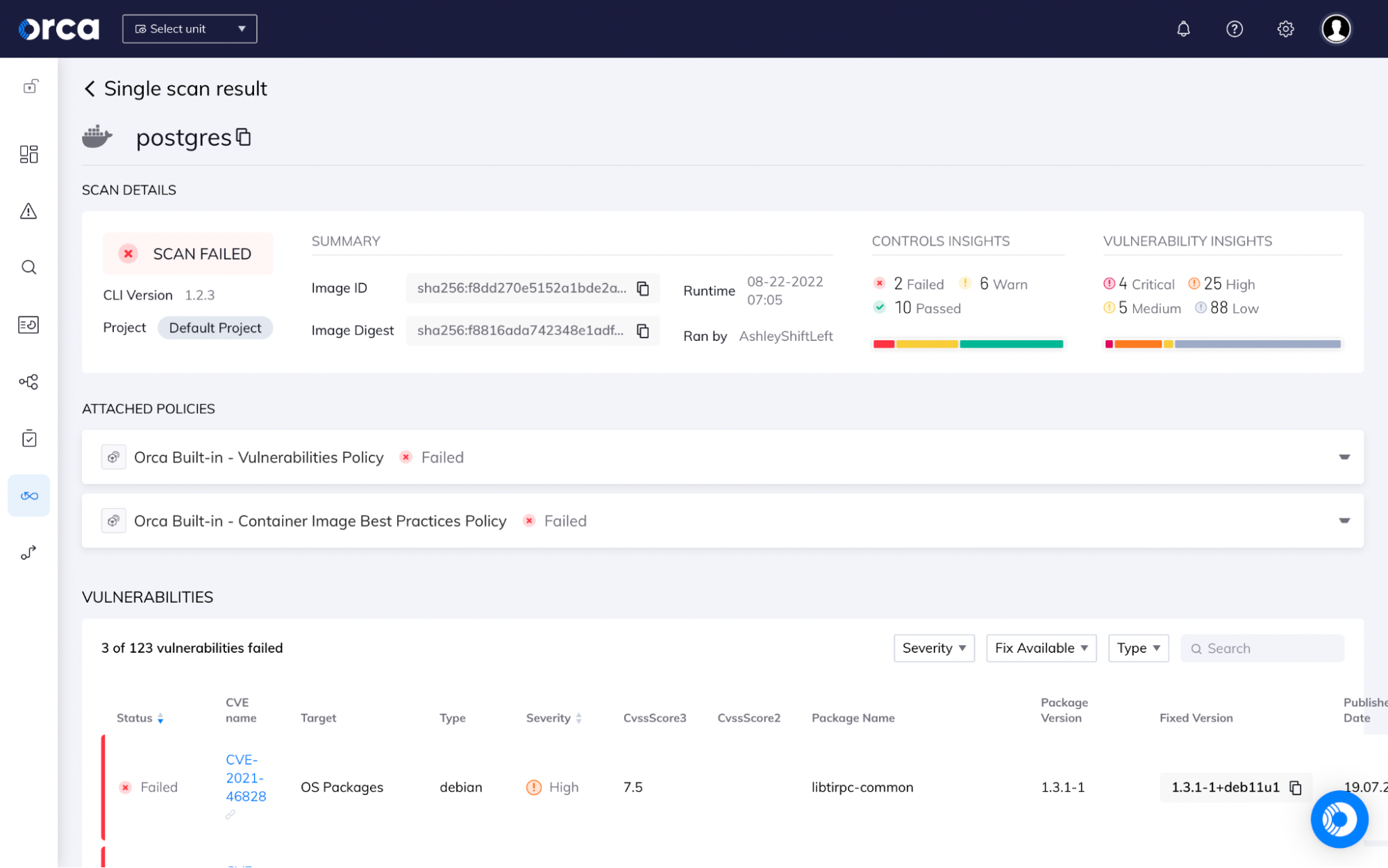
Build security into your CI/CD process
Embed comprehensive cloud security checks into your CI/CD process by leveraging the easy-to-use Orca command-line interface (Orca CLI) to:
- Automatically run all the critical security and compliance checks using CIS benchmarks and custom policies.
- Surface findings in native development tooling as well as the Orca Platform UI.
- Orca supports common CI and development tools, including Jenkins, BitBucket, CircleCI, GitHub, GitLab, and more.
Frictionless workflow integration
Orca offers a number of off the shelf integrations so you can fit Orca into your existing workflows, ensuring fast remediation and avoiding confusion about team responsibilities.
- Forward findings to notification systems such as email, PagerDuty, OpsGenie, and Slack.
- Auto assign alerts to remediation teams with ticketing systems such as Jira or ServiceNow.
- Apply security policy directly in GitHub using the native Orca GitHub app
- Automate remediation by integrating Orca with SOAR systems, including Torq and Brinqa
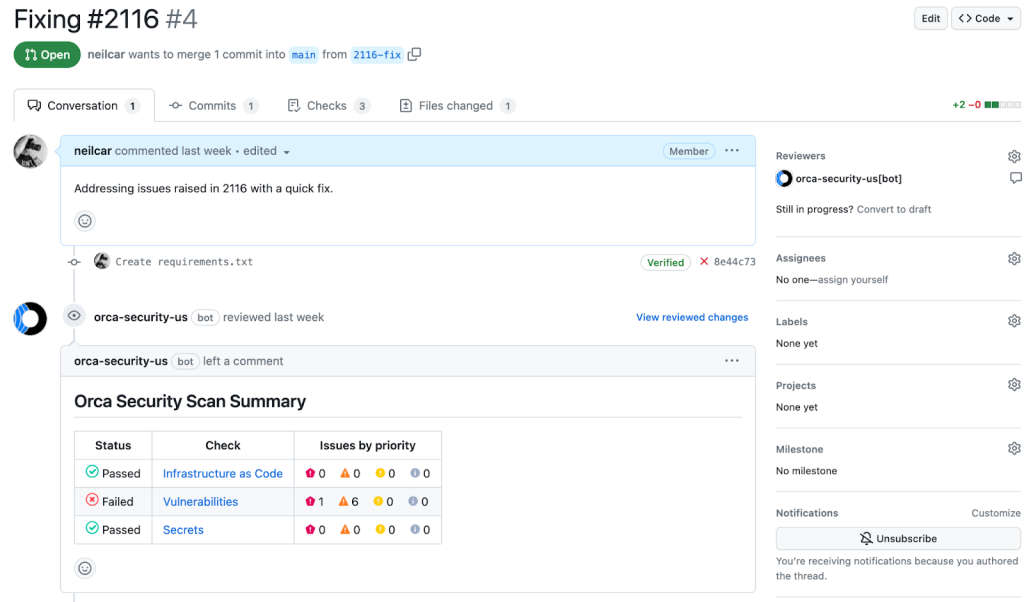
Orca Simplifies DevOps and DevSecOps Tasks

Demo the Orca Platform
In just 10 minutes, you’ll see how Orca Security can revolutionize your cloud security strategy. Watch a recorded demo from a cloud security expert now.